top of page

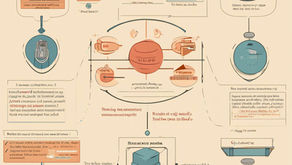
Homomorphic Encryption: Enabling Secure Data Computation Without Sacrificing Privacy
Discover how Homomorphic Encryption ensures data privacy while allowing secure computations.

Vishwanath Akuthota
Oct 29, 20244 min read


Exploring Homomorphic Encryption: Apple’s Privacy-Centric Approach to Machine Learning with Vishwanath Akuthota
Discover how Apple's innovative use of homomorphic encryption, explained by Vishwanath Akuthota.

Vishwanath Akuthota
Oct 29, 20244 min read


A Comprehensive Guide to HTTP Status Codes from Vishwanath Akuthota
Learn the ins and outs of HTTP status codes, from successful responses to client and server errors.

Vishwanath Akuthota
Oct 23, 20246 min read


Future-Proofing AI Strategies: Pioneering the Path to Success insights from Vishwanath Akuthota
Amidst the ever-changing field of technological advancements, Artificial Intelligence (AI) emerges as a pivotal force for transformation....

Vishwanath Akuthota
Oct 21, 20243 min read


Classification of Laws, Lok Adalat & Legal Aid, Rule of law -- Vishwanath Akuthota
Explore the intricate fabric of law with Vishwanath Akuthota, a visionary leader in AI and cybersecurity, as he bridges the gap between tech

Vishwanath Akuthota
Oct 19, 20246 min read


AI Shared Responsibility Model: Navigating Security and Layers
Delve into the AI Shared Responsibility Model and navigate the layers of security with confidence.

Vishwanath Akuthota
Jul 13, 20242 min read


Don't Get Fooled by a Single Pixel: One-Pixel Attacks
Discover the hidden dangers of One-Pixel Attacks and how they can deceive neural networks. Learn how Dr Pinnacle is combating.

Vishwanath Akuthota
Jul 12, 20242 min read


Exploring Ethical Considerations in AI Development
Uncover the ethical landscape of AI development and its impact on society. Dive into the complexities of AI ethics to shape a responsible AI

Vishwanath Akuthota
Jul 1, 20243 min read


Kali Linux 2024.2 with 18 new tools
Unveiling Kali Linux 2024.2 with 18 new tools! Explore the latest arsenal for cybersecurity experts. Stay ahead of threats with Kali Linux.

Vishwanath Akuthota
Jun 6, 20244 min read


The Growing Movement of Data Poisoning: Artists Fight Back Against Generative AI
In recent years, the rise of generative AI has brought both excitement and concern across various industries. While these advanced algorithm

Vishwanath Akuthota
May 29, 20243 min read


The Smurf Attack: What You Need to Know
Discover the ins and outs of the notorious Smurf Attack and how to safeguard your network from this crippling DDoS threat. Learn more now!

Vishwanath Akuthota
Apr 26, 20243 min read


QUIC: Quick UDP Internet Connections
Quicmap is a command-line tool written in python that can be used to scan networks for QUIC services. QUIC (Quick UDP Internet Connections)

Vishwanath Akuthota
Mar 19, 20242 min read


🔰7 Best Hacking Tools Everyone Must Know🔰
7 Best Hacking Tools Everyone Must Know

Vishwanath Akuthota
Mar 9, 20241 min read


BobTheSmuggler: Open-Source Tool for Undetectable Payload Delivery
BobTheSmuggler: Open-Source Tool for Undetectable Payload Delivery

Vishwanath Akuthota
Mar 2, 20242 min read


Routing in a nutshell
Routing

Vishwanath Akuthota
Oct 29, 20232 min read


WiFi Deauthentication Attacks Using Kali Linux
Deauthentication Attack

Vishwanath Akuthota
Oct 11, 20237 min read


What is NMap and Cheat Sheet
In the ever-evolving world of cybersecurity and network management, having the right tools in your arsenal is crucial.

Vishwanath Akuthota
Oct 9, 20234 min read


Adversarial Attacks in Machine Learning: Understanding Impact and Mitigation Strategies
Adversarial Attacks in Machine Learning

Vishwanath Akuthota
Sep 26, 20233 min read


How Intrusion Detection Systems (IDS) Can Help Your Organisation
Intrusion detection systems (IDSs) are an essential part of any organisations cybersecurity arsenal. They can help to detect and prevent...

Vishwanath Akuthota
Sep 5, 20233 min read


Safeguarding Large Language Models: Understanding and Mitigating Potential Attacks
Large language models have revolutionized the field of Natural Language Processing (NLP) and Artificial Intelligence (AI), empowering us...

Vishwanath Akuthota
Jul 21, 20232 min read
bottom of page